Infineon Tpm
Contents • • • • • • • • • • • • • • • History [ ] Trusted Platform Module (TPM) was conceived by a consortium called (TCG), and were standardized by (ISO) and (IEC) in 2009 as ISO/IEC 11889. TCG continued to revise the TPM specifications.

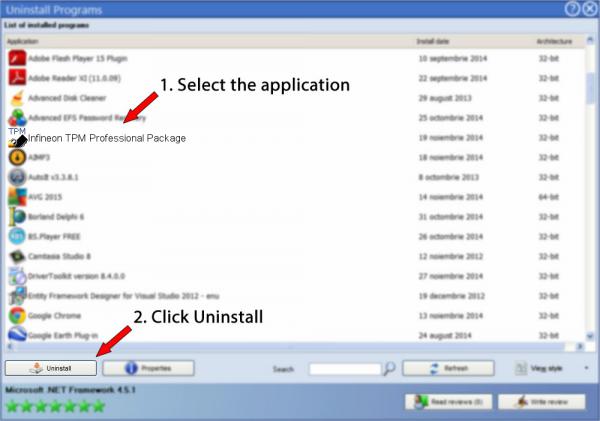
Solved: Dear all, While trying to update to Win10 1709 I get error that Infineon TPM need to be uninstalled - manually How do I uninstall this? Infineon TPM Professional Package is a program developed by Infineon Technologies. Custom Cars And Cycles Zip there. The most used version is 4.3.000.3137, with over 98% of all. Infineon announced that its TPMs have been generating insecure RSA keys, affecting Lenovo, HP, and Fujitsu devices. An updated firmware is available via the latest Windows patch bundle, but users will have to clear their old TPM keys after updating. A security vulnerability has been identified which affects the RSA key generation in some Infineon® developed Trusted Platform Modules (TPM).
The last revised edition of TPM Main Specification Version 1.2 was published on March 3, 2011. Katzenjammer Le Pop Album more. It consisted of three parts, based on their purpose. For the second major version of TPM, however, TCG released TPM Library Specification 2.0, which builds upon the previously published TPM Main Specification. Its last edition is released on October 1, 2014, with an followed up on June 1, 2015. Overview [ ] Trusted Platform Module provides • A • Facilities for the secure generation of for limited uses.
•: Creates a nearly unforgeable summary of the hardware and software configuration. The software in charge of hashing the configuration data determines the extent of the summary. This allows a third party to verify that the software has not been changed. • Binding: Encrypts data using the TPM bind key, a unique key descended from a storage key [ ]. •: Similar to binding, but in addition, specifies the TPM state [ ] for the data to be decrypted (unsealed). Computer programs can use a TPM to hardware devices, since each TPM chip has a unique and secret key burned in as it is produced.
Pushing the security down to the hardware level provides more protection than a software-only solution. Uses [ ] The (DoD) specifies that 'new computer assets (e.g., server, desktop, laptop, thin client, tablet, smartphone, personal digital assistant, mobile phone) procured to support DoD will include a TPM version 1. Do Facebook Pdi Gratis. 2 or higher where required by and where such technology is available.' DoD anticipates that TPM is to be used for device identification, authentication, encryption, and device integrity verification. Platform integrity [ ] The primary scope of TPM is to assure the integrity of a platform. In this context, 'integrity' means 'behave as intended', and a 'platform' is any computer device regardless of its. It is to ensure that the starts from a trusted combination of hardware and software, and continues until the operating system has fully booted and are running. The responsibility of assuring said integrity using TPM is with the firmware and the operating system.